
Auditmation transforms your burden into a frictionless 3rd Party audit management reality.
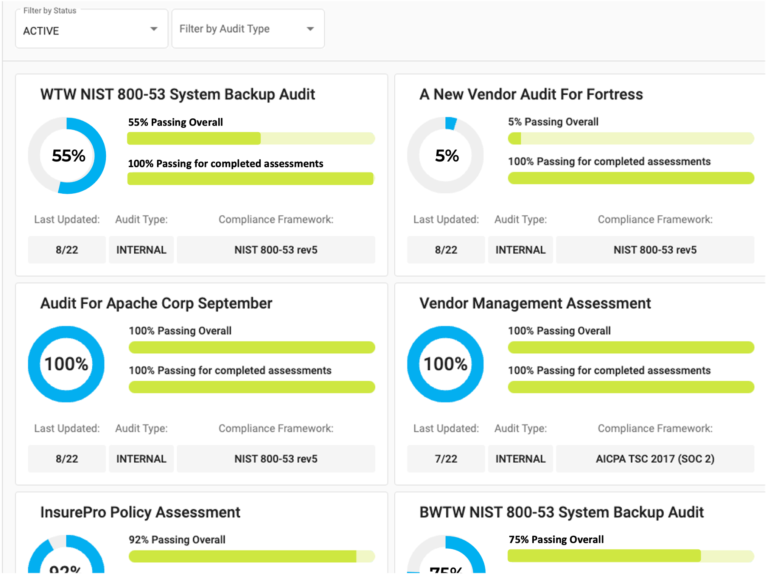
Auditmation enables internal security and compliance teams to transform cyber security assessments by initiating mechanized audits (in minutes) that provide
pre-selected least privilege data and risk analytics access to policy underwriters, at any given time.
Whether risk underwriters require access and backup of a critical database with PII data or continual assurance of key cyber hygiene controls, organizations become empowered provide machine-validated "self protection" evidence with the click of a mouse.

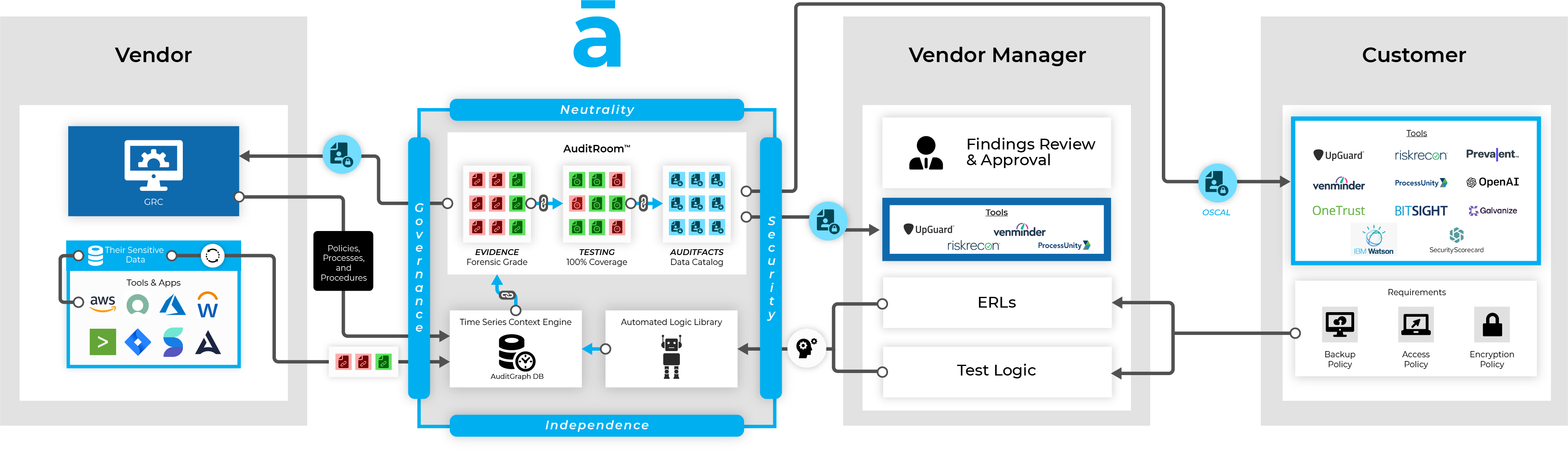
Quickly provide direct access and visibility to their highly sensitive data
Machine validate the implementation and use of critical controls
Easily provide continual access to the data that matters most
Every piece of evidence has complete forensic chain of custody

Operational GRC tools like Drata, Tugboat, and Anecdotes try to force auditors to learn the nuances of each of their systems across a multitude of audits.
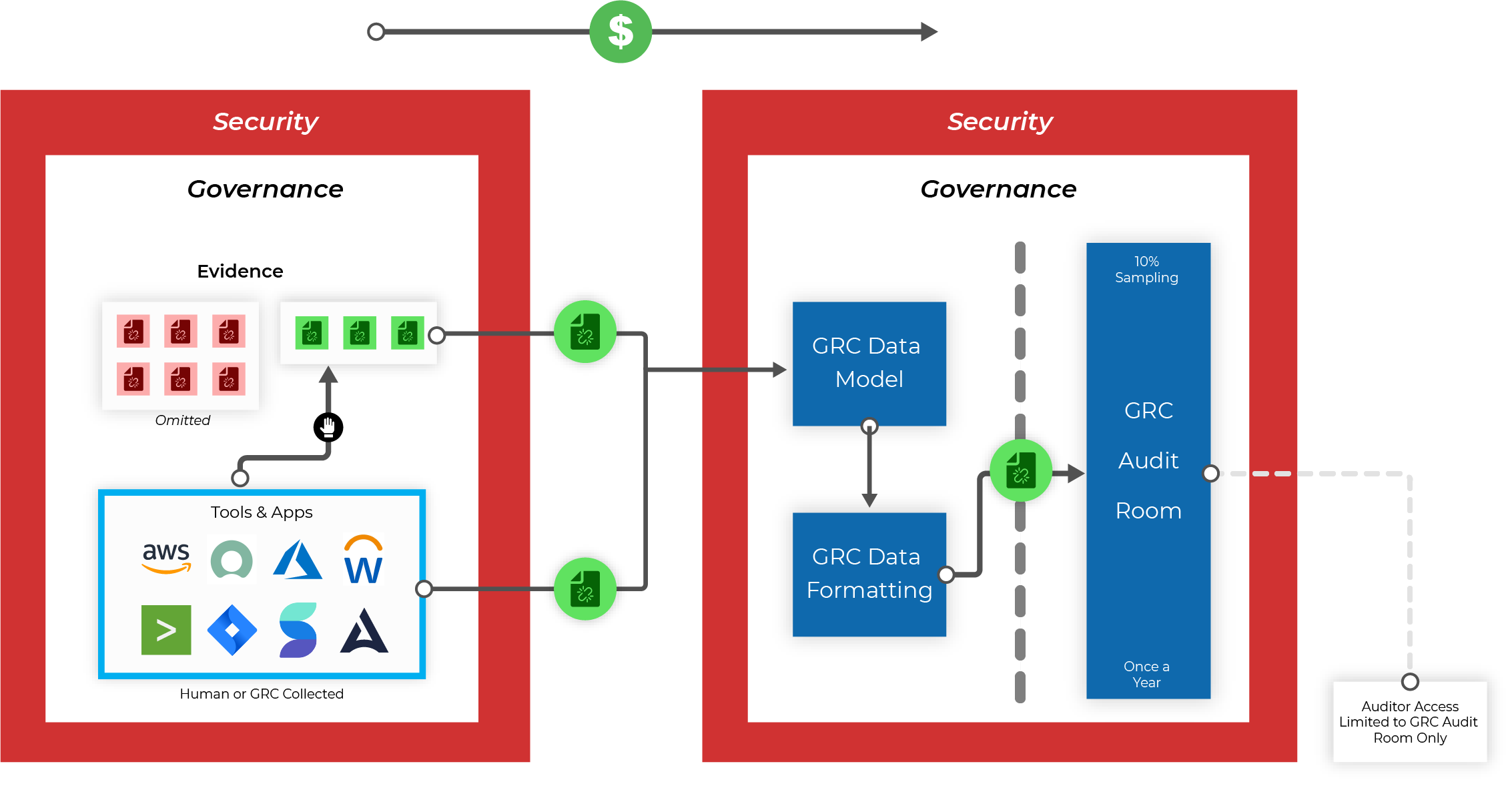
Auditors force auditees to manufacture and ship data to hundreds of audit rooms. No centralized platform to stitch models and tools to unlock all parties in the ecosystem.
Auditee pays Auditor, and GRC tools that collect evidence on their behalf
10% population sampling omits 90% of all relevant evidence
Human-based audit processes drive bias, risk, and do not scale
Human and GRC collected evidence has no forensic chain of custody
Annual audits bring little to zero value to cyber readiness
Gated access hides the truth, dependent on Auditee evidence and quality
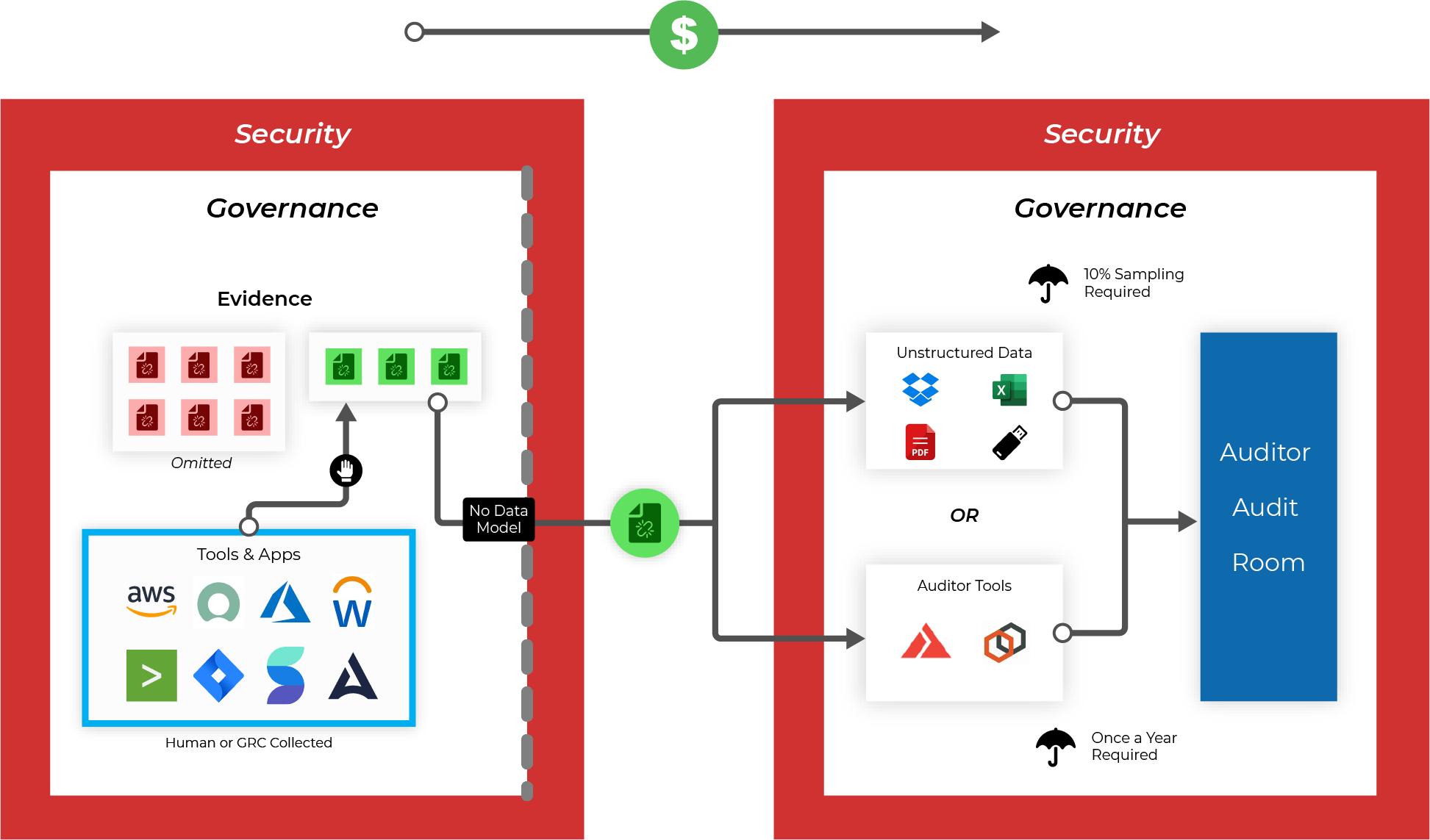
Leverage an IT Audit Data platform to evidence collection on critical data or applications
Centralize automated evidence into a single data catalog that supports any application or renewal process
Grant real-time auditor assessment access directly to your evidence systems and/or audit room

Headquartered in Austin, TX, Auditmation is the 3rd party IT audit and risk automation data platform enabling auditors, advisory and risk tools to strengthen audit integrity and independence in a neutral, mechanized data room.Automated evidence and testing creates higher value, tech-enabled audit and risk assurance services for our partners, that reduces the audit burden and drives cyber risk out of their client organizations and vendors, through ZeroBias™ audit data quality.
The Auditmation™ platform is available exclusively through our audit, advisory, and technology partner network.
View our Privacy Policy or Transparency of Coverage
(888) 988-8647
sales@auditmation.io
zerotrust@auditmation.io (Working group)
Auditmation
12400 Highway 71 West
Suite 350-407
Austin, TX 78738
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |